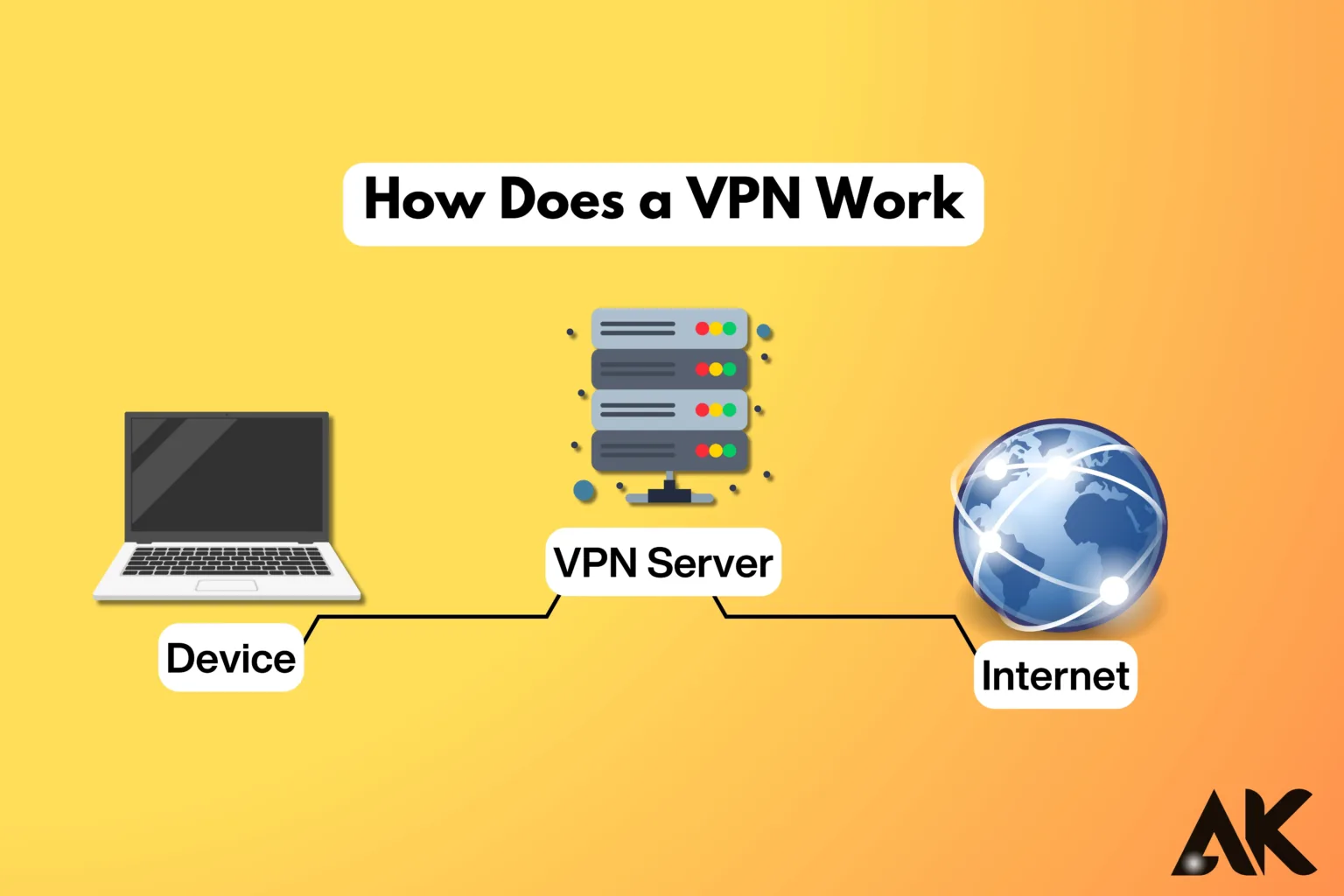
How does a VPN work? A virtual private network, or VPN, is an effective tool that improves your online privacy and security by providing a safe, encrypted connection between your device and the internet. Whether browsing from home, a coffee shop, or on public Wi-Fi, consider it a protective tunnel that keeps your data safe from prying eyes. When you use a VPN, it reroutes your internet traffic through a secret server, hiding your IP address and making your online actions essentially untraceable.
This enables you to view stuff that could be blocked in your area while still protecting private information like passwords and bank account information. Whether you want to stream shows from another nation, want to be anonymous, or are worried about cyber dangers, the first step to taking charge of your digital life is learning how a VPN works. We’ll explain the inner workings of a VPN and why it’s a necessary tool in today’s connected world in this short guide.
How does a VPN work?
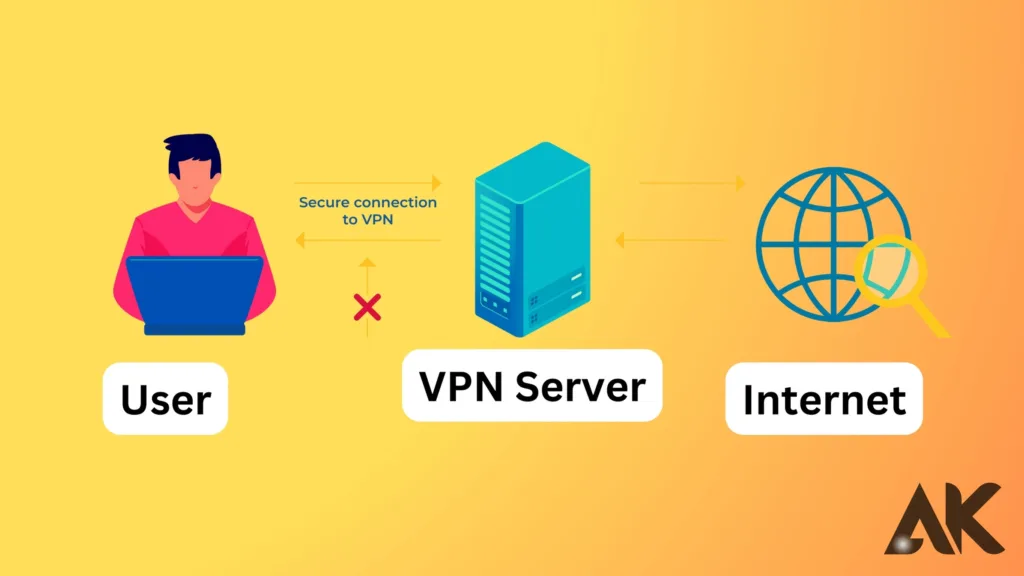
How does a VPN work? When you connect to a VPN via its desktop program or app, it encrypts your internet connection. Your traffic moves back and forth across that encrypted connection, the virtual tunnel that connects your device to the server of your choice, effectively hiding your IP address and online activities from other parties.
In a process known as a “handshake,” your device and the VPN server exchange encryption keys when you connect to them. This is how the process operates. This instantaneous handshake procedure is crucial because it ensures that only the VPN server can decrypt the data you send from your device, and only your device can decode the data the VPN server sends back.
The handshake completes the creation of your secure internet tunnel. Your device encrypts your data before it leaves. The VPN server receives it via a tunnel, decrypts it, and then sends it back to the website you are currently on. After that, the website transfers data to the VPN server, which encrypts it before sending it back to your device over the tunnel. The webpage data is encrypted, so you can read it once it reaches your device.
How a VPN Can Help You Protect Your Online Identity

When you use the internet, your ISP receives the information you send or request via a web browser to any server (like when you search on Google), along with your request, IP address (like your laptop or mobile device), and destination IP address (like Google). After monitoring all your activities, the ISP forwards your request to the destination IP address and retrieves the data in the same way. Your ISP acts as an intermediate station for all of your data. They have access to all of your internet usage history and current usage patterns.
But that isn’t the case when you’re using a VPN. Any request you send to a website or server first goes through the VPN server before connecting to the server itself. The VPN server encrypts all your information and requests before forwarding them to the website of your choice. Your ISP continues to monitor the situation. However, if you’re using a VPN, it will automatically encrypt the destination IP address and alter it to another IP address. This method prevents your ISP from reading it, leading them to assume that the VPN’s IP address is the source of all your requests. Therefore, the VPN will receive all your requests.
What are VPN protocols?
The protocols are another crucial component of the VPN puzzle. In essence, they are procedures and orders that determine how web traffic moves across an encrypted tunnel between servers.
Although there are several VPN protocols available, the following are the most often used:
- Transport Layer Security (TLS) and Secure Sockets Layer (SSL)
- Protocol for Point-to-Point Tunneling (PPTP)
- IP Protection (IPSec)
- Layer 2 Tunneling Protocol (L2TP) Internet Key Exchange (IKEv1 or IKEv2)
- OpenVPN’s WireGuard
However, VPN services are constantly evolving, and the introduction of new protocols often renders existing ones obsolete. NordVPN asserts that all protocols possess potential vulnerabilities, either documented or undiscovered, which could potentially compromise your security.
How do VPNs unblock streaming sites?
But VPNs are capable of much more than merely encrypting your data. Additionally, you won’t have to worry about annoying geo-restrictions to access a variety of streaming sites and their region-locked libraries. The show is quite simple. The majority of high-end VPNs have thousands of servers spread out throughout the world. You will receive a new IP address located in the same place if you connect to one of these servers. This allows you to access country-specific services by tricking websites into believing you are there as well.
For instance, you must connect to a VPN server in the US if you’re in the UK and wish to view what’s available on US Netflix. Since you have a US IP address, Netflix will assume you are in the US when you refresh. The greatest American Netflix material will be presented to you in an easy-to-understand manner.
How VPNs work—in a nutshell
By using its servers, a VPN reroutes your traffic from the servers of your ISP. Furthermore, the VPN encrypts the traffic, ensuring that anyone intercepting it cannot read it. VPNs transfer your data using a variety of protocols; the industry leaders today are OpenVPN and WireGuard.
Although the main purpose of VPNs is to safeguard your private information, many individuals also use them to unblock streaming media from other countries. Global networks of servers operated by a specific VPN provider make this possible. You can join a server in another country, get an IP address there, and fool websites into believing you’re physically there as well.
How a VPN Works
A VPN operates by establishing a safe, encrypted connection between your device and the internet. To guarantee that your data is secure and private, this method combines some steps and technologies. The following methods are used to enable VPN capabilities:
- Step 1: Device Connection to a VPN Server
Your device first creates a connection with a VPN server when you turn on a VPN. Usually, you can choose a server located in a different region, or the VPN service can handle it for you.
- Step 2: Data Encryption
The VPN client software uses modern encryption algorithms to protect your data before it leaves your device. Without the right decryption key, it is practically impossible to intercept and read this encrypted data.
- Step 3: Data Transmission to the VPN Server
The VPN server receives the data after encryption. This server serves as a bridge connecting your device to the internet.
- Step 4: IP Address Masking
The VPN server substitutes its IP address for yours. This implies that your data will appear to be coming from the VPN server’s location rather than your actual location when it reaches the target server (such as a website).
- Step 5: Data Decryption
The VPN server encrypts data before returning it to your device after receiving it from the internet (for example, a webpage you requested).
- Step 6: Final Decryption
You can access the content as though you were physically connected to the internet when your VPN client decrypts the data it got from the VPN server.
Can I use a VPN on my phone?
It is possible to utilize a VPN on a mobile device, such as a tablet or phone. Whether your phone is running iOS or Android, any reputable VPN provider will have an easy-to-use mobile app that you can download. We would advise utilizing the IKEv2 protocol whenever possible when running a VPN on your phone, even though it isn’t as objectively secure as the OpenVPN protocol.
This is because it is dependable, quick, and secure, and it will maintain its connection even if you switch between Wi-Fi and cellular data. Because of that latter criterion, IKEv2 is the perfect protocol for mobile devices. All leading VPN providers support the IKEv2 protocol, ensuring seamless connection when using a VPN on your mobile device.
What are the different types of VPNs?
Although there are many other types of VPNs, the most popular ones are consumer or personal VPNs like ExpressVPN, NordVPN, Proton VPN, and Surfshark. Below is a list of the various types of virtual private networks.
Personal VPNs:
- Also referred to as consumer VPNs, these link you to a server via a client or application. Selecting a server location from the list encrypts your web traffic. For basic privacy, unblocking streaming content, getting around censorship, and getting around throttling limits, the majority of people utilize personal VPNs.
Remote access VPNs:
- In the office, a remote access VPN is usually used to access data, such as file servers, from any location or to work from home using an encrypted connection. For example, an IT specialist might use a remote access VPN to install software on your computer, creating the illusion of two geographically separated PCs connected to the same local network.
Site-to-site VPNs:
- A site-to-site VPN connects multiple physical offices (sites). There are intranet site-to-site VPNs that connect the local networks of various places, such as a company’s satellite offices. With safeguards in place to restrict access for outside organizations, extranet site-to-site VPNs enable online and external parties, such as a business and its clients, to share resources from around the globe.
Conclusion
How does a VPN work? A VPN is an essential tool for anyone looking to enhance their online security, protect their privacy, and access content without restrictions. By creating a secure and encrypted tunnel for your data, a VPN keeps your personal information safe from hackers, advertisers, and even your internet service provider. It effectively masks your IP address, making it difficult for anyone to trace your online activities, while also allowing you to bypass geographic restrictions and censorship.
Whether you’re streaming content, shopping online, or simply browsing the web, a VPN provides a sense of security in a world where digital threats are ubiquitous. Easy to set up and use, it’s a simple yet powerful way to control your online experience and ensure that your data remains yours and yours alone and only yours.
FAQ
Q1: What is a VPN, and why should I use it?
A VPN, or Virtual Private Network, is a service that creates a secure, encrypted connection between your device and the internet. It helps protect your privacy, secures your data, and allows you to browse the web anonymously. Using a VPN is especially useful when using public Wi-Fi or accessing restricted content.
Q2: Is it legal to use a VPN?
Yes, using a VPN is legal in most countries. However, in some places, like China or Russia, strict regulations surround the use of VPNs. Always check the local laws to ensure you’re complying with them when using a VPN.
Q3: Can using a VPN slow down my internet speed?
A VPN can marginally slow down your internet because it encrypts your data and passes it through a secret server. High-speed servers are available from many VPN providers, though, and with a solid VPN, the speed difference is typically negligible and well worth the extra security.
Q4: Can I avoid hackers using a VPN?
Indeed, a virtual private network (VPN) helps shield your data from hackers, particularly when you use public Wi-Fi. Encrypting your internet connection makes it considerably more difficult for thieves to intercept your private data, including passwords and financial information.
Q5: Is a VPN necessary for regular internet use?
Using a VPN for regular internet use can greatly improve your privacy and security; however, it is not strictly required for everyone. A VPN is a useful tool if you frequently use public Wi-Fi, wish to access geoblocked content, or are worried about your online privacy.